Question:
Can I use SSL with Spitfire sfPMS?
Answer:
Yes. In fact Spitfire strongly encourages use of SSL.
SSL can be used to protect all the data transmitted between the client and server by Spitfire users. The Internet address (URL) for the Spitfire site changes from HTTP: to HTTPS: and the default port changes from 80 to 443.
Many variations are possible, but the most common is described here. Specifically, we recommend that IIS be configured with SSL not required.
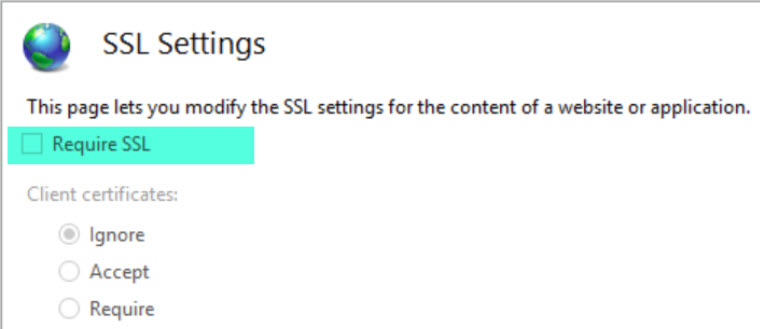
This allows mixed communication between clients and the IIS server. Once configured to use SSL, sfPMS will always redirect traffic through the login page to a secure connection. Additional configuration is required if all internal traffic uses SSL.
In order to enable SSL:
These instructions assume you have a functioning non-SSL site.
- You need to decide exactly what the host name of the Spitfire IIS server will be. For example, if the domain name is acme.com, you might choose spitfire.acme.com. This host name is associated with the website on the IIS server where the Spitfire site(s) will reside. Normally, this is not the default website.
- You need to apply for an SSL certificate from a certificate authority such as thawte.com, comodo or verisign.com. This procedure is done on the IIS server and the certificate authority‘s website. Depending on the certificate type, the processes can take minutes or hours or days. The certificate authority charges a fee for this service and the certificate must be renewed from time to time.
- Follow documentation provided by certificate authority to deploy the SSL certificate onto your server(s).
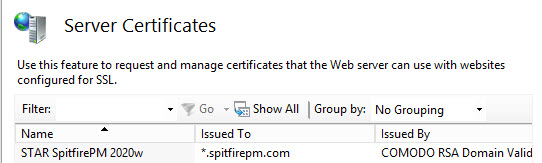
- Once you have an SSL certificate deployed, verify that you have deployed it correctly. Open the Server Certificate feature in INETMGR and look for your certificate. If it is not there, go back to your deployment steps.
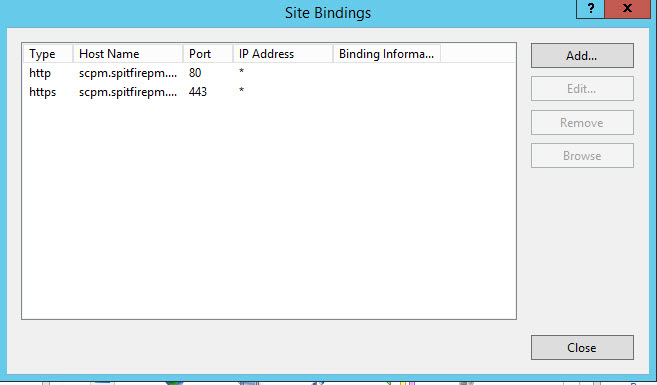
- In INETMGR open the Site Bindings dialog and add the host name with type as https and the required server name indication checkbox checked.
- Test your work so far:
- Use Chrome and a URL such as https//yoursite.spitfirepm.com/sfPMS/. You should reach the login prompt on a secure page. If it fails, go back and review all the previous steps. If it works, continue with the next step.
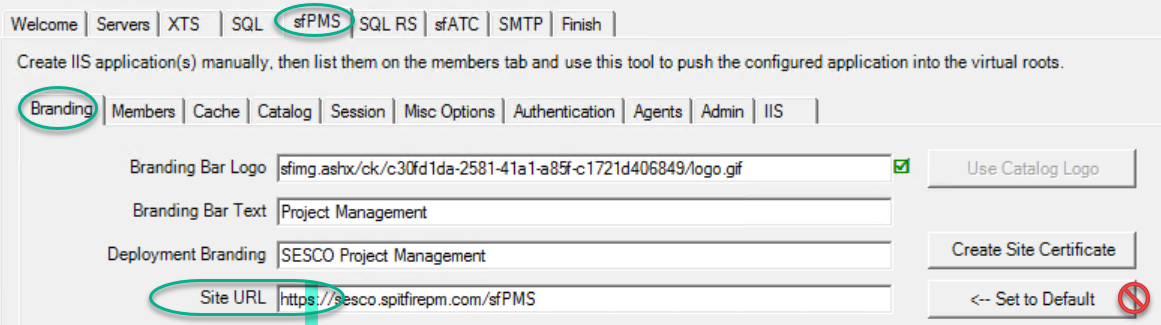
- Open ICTool and go to the sfPMS tab.
- On the Branding sub-tab, change the Site URL to start HTTPS. Do not click the Set to Default button yet!
- On the Members sub-tab, check the SSL checkbox. Do NOT change the PORT, see Farm Traffic below.
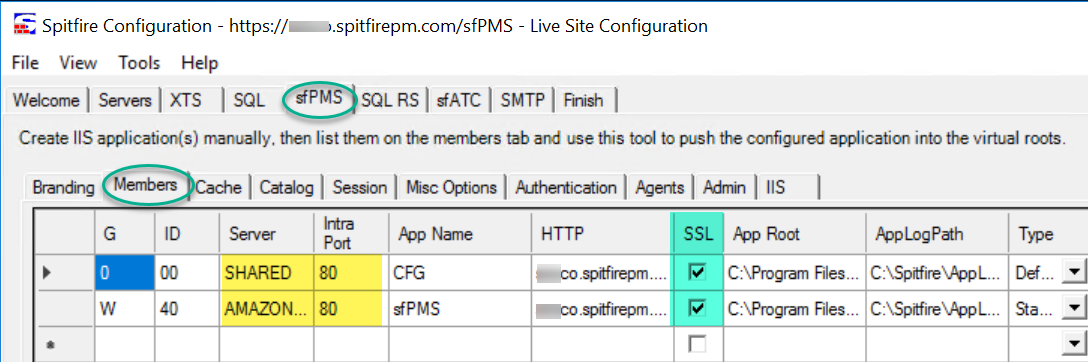
- Go to the Finish tab and re-publish the site.
- On the Branding sub-tab, change the Site URL to start HTTPS. Do not click the Set to Default button yet!
- Final test: Open sfPMS. When you reach the login page you should observe that the URL starts with https.
Keep in mind that SSL does add additional overhead to the IIS server, Internet traffic and the client. In most cases, the additional overhead is not noticeable.
Intra-Farm Traffic
In a farm, and with XTS enabled, message are sent to the member sites using the SERVER NAME and PORT. This works well on port 80 unless you also check the INETMGR “require ssl” option. If so, also set the port column to 443 and verify that you have a viable binding for the site using the server name. An internal certificate may be required.
sfATC Service
Similarly, sfATC normally communicates with the sfPMS web application using internal traffic, often via loopback or localhost. No changes are required on the sfATC tab unless you also check the INETMGR “require ssl” option. If so, check the “requires SSL” option on the sfATC tab and change the URL to one that matches a viable SSL binding.
Additional Comments:
This article does not take into account advanced configurations and environments that include Internet Acceleration Server (IAS) and/or web farms. Spitfire is capable of running in these advanced configurations, but details are beyond the scope of this article.
KBA-01290; Last updated: November 19, 2018 at 18:04 pm;
Keywords: SSL;HTTPS;443;